Public Key Infrastructure Fundamental (Part 2)
This post is a continuation (par 2) of my post that can be found here. In this post, I am going to discuss about Public Key and Private Key.
As you can see from the above image, the public-key and private-key are both used in the encryption process in the PKI. One think you need to remember, we use the receiver's public-key as the key to encrypt the message. On the other side, the receiver, will decrypt the message using the private-key that he has.
To simplify things:
In an asymmetric key encryption scheme, anyone can encrypt messages using the public key, but only the holder of the paired private key can decrypt. Security depends on the secrecy of that private key.
Public Key
Public key can be defined as a value provided by some designated authority as an encryption key that, combined with a private key derived from the public key, can be used to effectively encrypt messages and digital signatures. Private key will be discussed below.Private Key
Private key can be defined as an encryption/decryption key known only to the party or parties that exchange secret messages.| Public-key Encryption Source: Globus |
To simplify things:
- Think of a public key as being the lock. It’s not actually a key, it’s a padlock you can make lots of copies of and distribute wherever you want.
- Think of a private key as being the actual key. This is what you use to open the padlock that is stored on the other machine. Just like a regular key you keep it secret, safe, and out of the wrong hands.
| Public-key Encryption Source: Wikimedia |
In an asymmetric key encryption scheme, anyone can encrypt messages using the public key, but only the holder of the paired private key can decrypt. Security depends on the secrecy of that private key.
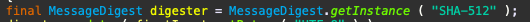
Simple explanation. Nice share :)
ReplyDelete