Public Key Infrastructure Fundamental (Part 1)
Public key infrastructure is an infrastructure developed to ensure the data security that is being transfered within insecure network.
If we talk about PKI, we will talk about some common terms used in this area, such as encryption, digital signatures, public keys, private keys.
In Part 1 of this post, we will explore about the two terms, which are encryption and digital signatures. Public keys and private keys will be discussed in Part 2 of this post.
Encryption/decryption process has long been used in computer security to secure the data that is considered as private and can only be seen by certain persons. There are many algorithms exist to perform the encryption process, such as DES (Data Encryption Standard), 3DES (3 times encryption using DES), and AES (Advanced Encryption Standard). AES actually supersedes as standard encryption algorithm used by US Government.
The AES algorithm is commonly known as symmetric-key algorithm. Symmetric-key algorithm is an algorithm for that use shared secret-key to encrypt and decrypt the data. 3DES is one algorithm that is known to use symmetric-key concept. Other algorithms are blowfish, twofish, CAST-128, and IDEA.
Public-key cryptography, on the other hand, uses two different key to encrypt and decrypt the data. One used to encrypt is know as public key, whilst the other is known as private key. One algorithm that is known to use public-key cryptography is RSA. RSA stands for Ron Rivest, Adi Shamir and Leonard Adleman. They are the ones to publicly described it in 1978.
| Public-Key Infrastructure Source: Wikimedia |
If we talk about PKI, we will talk about some common terms used in this area, such as encryption, digital signatures, public keys, private keys.
In Part 1 of this post, we will explore about the two terms, which are encryption and digital signatures. Public keys and private keys will be discussed in Part 2 of this post.
Encryption
Encryption can be considered as a process to disguise something as something else. This is most likely similar with people write letter to other using words that are understood just between them. This way, even if the letter is being stolen, the bad guy will not be able to read it and understand the content of it. Besides encryption, there is another term known as decryption. Decryption is basically the reverse process of encryption. It means that, we try to reverse the letter that is encrypted using strange words back to normal words that can be understood by human brain easier (or, in computer context, can be read by the computer, though it's not essentially the whole concept).Encryption/decryption process has long been used in computer security to secure the data that is considered as private and can only be seen by certain persons. There are many algorithms exist to perform the encryption process, such as DES (Data Encryption Standard), 3DES (3 times encryption using DES), and AES (Advanced Encryption Standard). AES actually supersedes as standard encryption algorithm used by US Government.
The AES algorithm is commonly known as symmetric-key algorithm. Symmetric-key algorithm is an algorithm for that use shared secret-key to encrypt and decrypt the data. 3DES is one algorithm that is known to use symmetric-key concept. Other algorithms are blowfish, twofish, CAST-128, and IDEA.
Public-key cryptography, on the other hand, uses two different key to encrypt and decrypt the data. One used to encrypt is know as public key, whilst the other is known as private key. One algorithm that is known to use public-key cryptography is RSA. RSA stands for Ron Rivest, Adi Shamir and Leonard Adleman. They are the ones to publicly described it in 1978.
| Public-Key Encryption Source: Globus |
Digital Signatures
Digital signature, as the name describes, is just like a human signature but in a digital format. This signature is used to proof the authenticity of the data that is transfered over the network. Valid digital signatures means that the data is the same as it is transfered by the sender and not being altered by irresponsible person.
As can be seen from the above diagram, the concept of digital signature is quite simple. The data's signature will be computed using hash algorithm and then encrypted using the signer's private key. The receiver will then decrypt the signature using the signer's public key and compare the value with the computed has value of the received data. If the value are the same, then the received can pretty sure that the data is valid and not tampered along the way.
Below are some reasons to use digital signatures:
| Digital Signature Concept Source: Wikimedia |
As can be seen from the above diagram, the concept of digital signature is quite simple. The data's signature will be computed using hash algorithm and then encrypted using the signer's private key. The receiver will then decrypt the signature using the signer's public key and compare the value with the computed has value of the received data. If the value are the same, then the received can pretty sure that the data is valid and not tampered along the way.
Below are some reasons to use digital signatures:
- Authentication. By using the digital signature, we can make sure that the data sent is owned by specific user that is considered to be the sender.
- Integrity. By using the digital signature, we can make sure that the data sent is not being tampered by irresponsible person when being transferred.
- Non-repudiation. By using the digital signature, we can make sure that the sender, at some time in the future, cannot decline that he already signed the data.
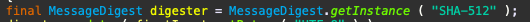
Comments
Post a Comment